Replace machine certificate in vSphere 7
Compared to posts that describe the same task in older versions, this will be a rather short one. Specially replacing vCenter certificates was getting more and more easier during versions. It has never been that easy!
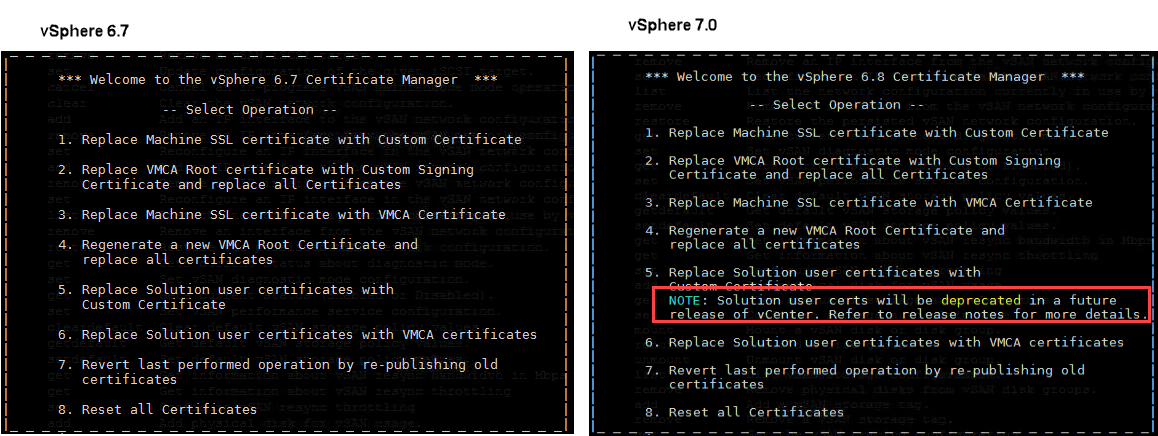
In vCenter 7 we just have one certificate to manage. Solution Certificates are gone, respectively are deprecated in 7.0 . You can also see in CLI certificate-manager. See welcome screen in 6.7 and 7.0:

In vSphere 7.0 there is also a new GUI to replace this certificate. This post will explain the steps to replace vCenter certificate by a certificate signed by a Windows CA.
Steps for replacement
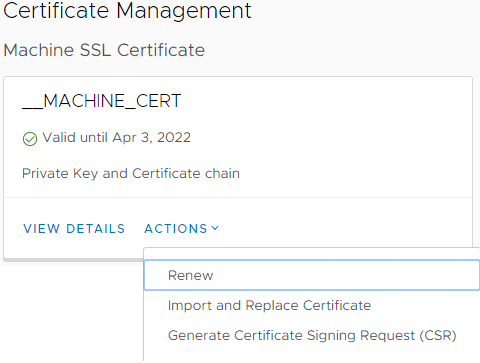
- Create an CSR (Certificate Signing Request) for the new certificate.To do so, go to Menu –> Administration –> Certificate Management and in press on ACTIONS in __MACHINE_CERT box:
 Select Generate Certificate Signing Request (CSR). Fill in requested data. Make sure to enter FQDN and short hostname (comma separated) of vCenter in Subject Alternative Name. This is because current browsers check this values to compare with actually hostname.
Select Generate Certificate Signing Request (CSR). Fill in requested data. Make sure to enter FQDN and short hostname (comma separated) of vCenter in Subject Alternative Name. This is because current browsers check this values to compare with actually hostname.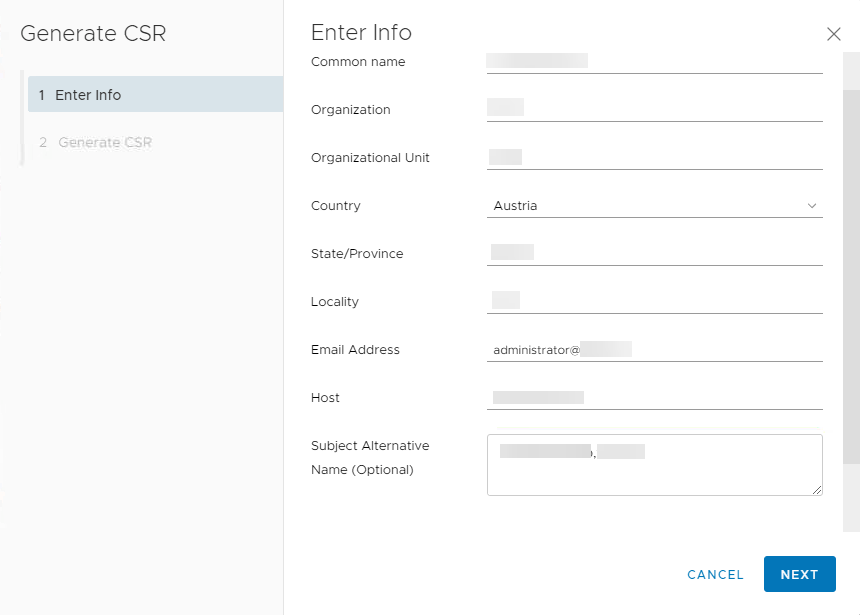 When pressing next, you have the option to copy request to clipboard and to download it.
When pressing next, you have the option to copy request to clipboard and to download it.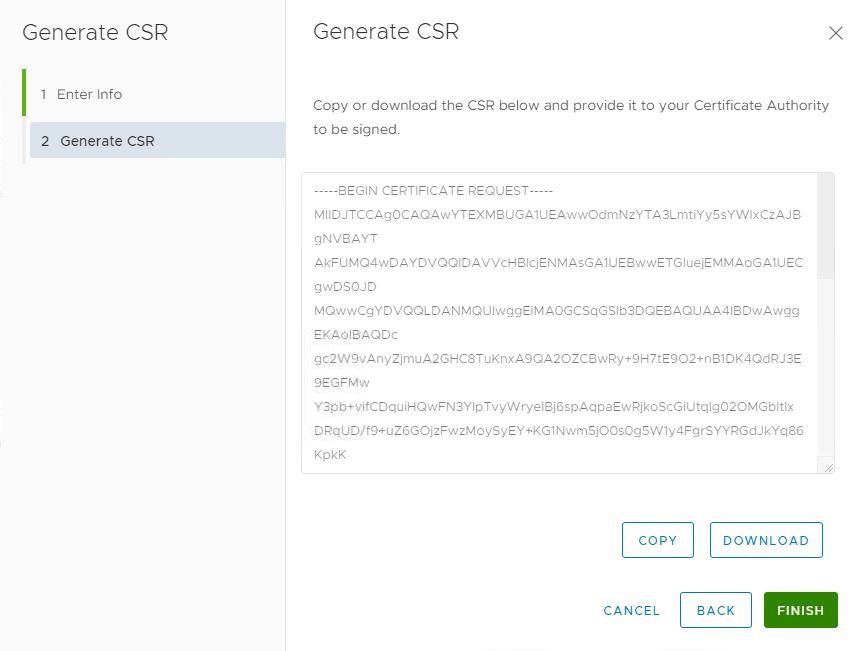
Download the file for usage in next step. Here: C:\Cert\vcsa.csr - Create new certificate in Windows CA
Up to now I used the Windows CA Web Enrollment Site (https://CA_hostname/certsrv/) for this task. But I was told this isn’t maintained by Microsoft any more. So I switched to a supported method: command line. Normally this can be done by using MMC, but doing so, you cannot define the certificate template to use (see Notes). Therefore I use the command: certreq. Full command to use Web Server template:certreq.exe -submit -attrib "CertificateTemplate:WebServer" "C:\Cert\vcsa.csr"This command will open a Save Certificate window. I use: C:\Cert\vcsa-cert.cer
- Export CA root certificate
Last piece we need is the CA root certificate (including existing chain). To get this (I also used Web Enrollment Site for this) we can use command line again. To export CA root certificate, run this command on CA computer:certutil -ca.cert c:\Cert\root-cert.cerUnfortunately we use another format (BASE64 – which is human readable). Therefore run this command to convert format:
certutil -encode c:\Cert\root-cert.cer c:\Cert\root-cert-base64.cer - Replace certificate
Last step is to use the new wizard for certificate replacement. Now click on ACTIONS in __MACHINE_CERT box and select Import and Replace Certificate.
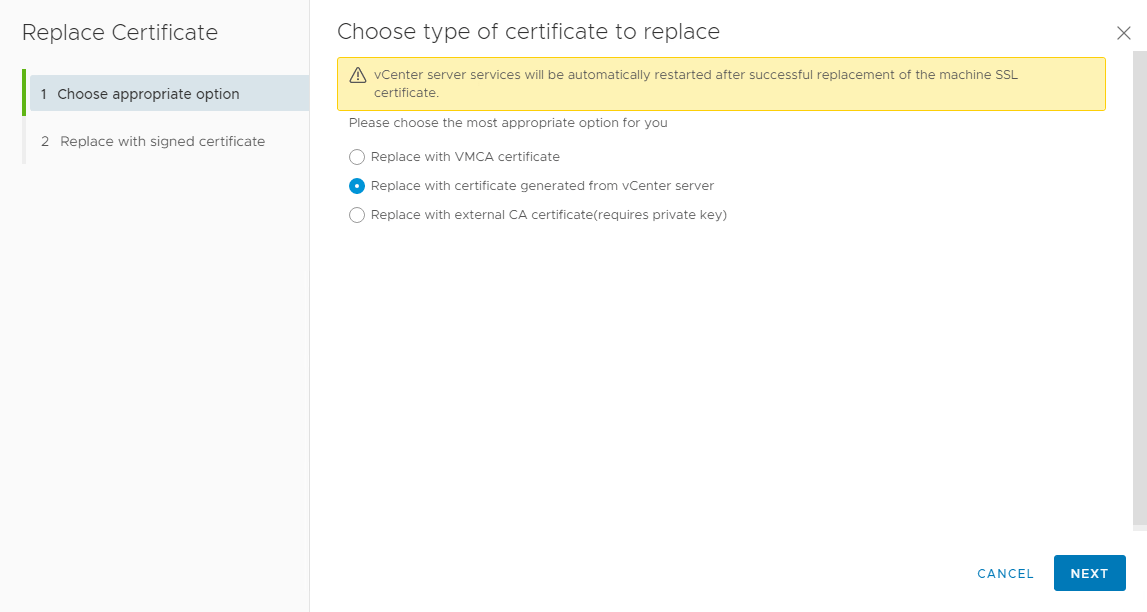
Select Replace with certificate generated from vCenter server. This sounds misleading, but is meant for the case, vCenter created the CSR that is used to create the certificate. And this is exactly what we did. With this option we do not need a private key because this is created during CSR creation.On next page, select appropriate files:
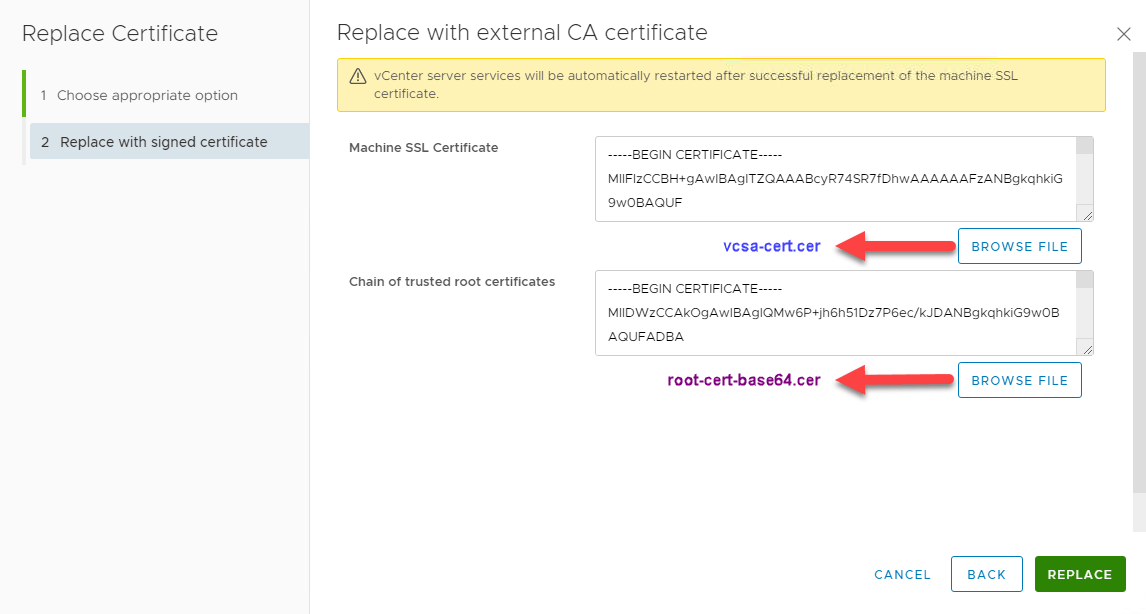
Machine SSL Certificate –> vcsa-cert.cer
Chain of trusted root certificates –>root-cert-base64.cerWhen everything works fine, all vCenter services will be restarted and you see this:
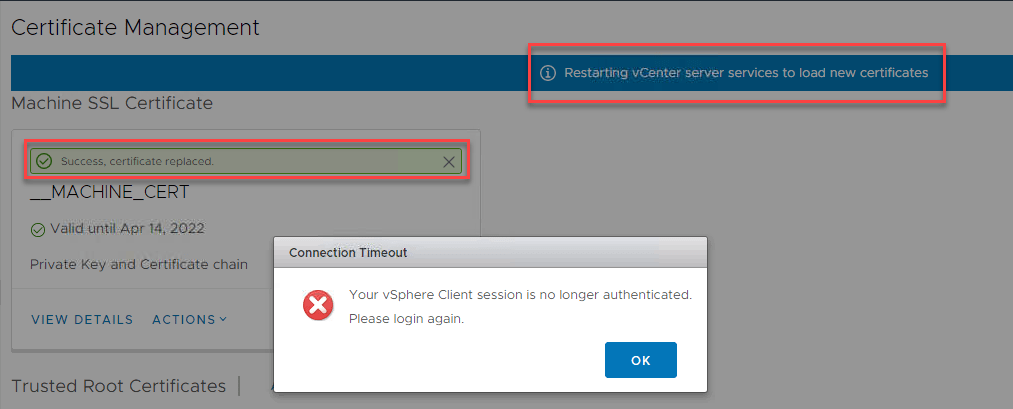
After a few minutes you should be able to login to vCenter again.
Notes
- After this procedure, you also see a new Trusted Root Certificate, which is CA root certificate.
- If you try to replace certificate this way without creation of a CSR, you will see this error:
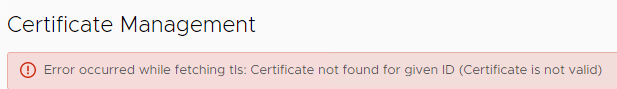
[Error occurred while fetching tls: Certificate not found for given ID (Certificate is not valid)] - To keep this workflow simple, you have to use the CSR to create the certificate. And you have to use this certificate for replacement. You must not create another CSR between certificate-creation and replacement. If you do so, you will see this error:
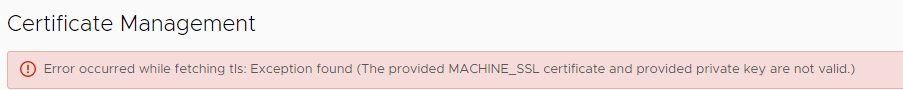
[Error occurred while fetching tls: Exception found (The provided MACHINE_SSL certificate and provided private key are not valid.)]This is because by creating a CSR, a private key will also be created. When you do another CSR creation after certificate-creation, private key does not fit anymore.
- If you try to issue certificate in Microsoft Certificate Authority GUI (MMC) you will get the following error – because of missing template information (See Step 2).
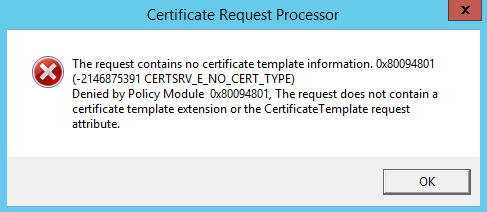
[The request contains no certificate template information. 0x80094801 (-2146875391 CERTSRV_E_NO_CERT_TYPE) Denied by Policy Module 0x80094801, The request does not contain a certificate template extension or the CertificateTemplate request attribute.] - Even when replacement works fine it could be that your browser shows certificate issues. This is a browser topic. For example Chrome do not like SHA1.
Same certificate is OK for Internet Explorer - [Update] When you search for the private key in VCSA during this process, read here to learn more. Post is for 6.7.
- [Update] If you run a intermediate CA that enrolls your certificate, you need to create a certificate chain for root CA. This chain must include root and intermediate CA certificate. You can simple copy .cer-file content of root and intermediate CA certificate into a single text file. I normally use the file extension .pem. Create this file in step 3.
If root certificate is not in chain during replacement, you will get the error:

[Error occured while fetching tls: the trustAnchors parameter must be non-empty]



Your blog mentions that Solution User certificates have gone in 7.0 but they’re still in the 7.0 documentation (https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.authentication.doc/GUID-3AF7757E-A30E-4EEC-8A41-28DA72102520.html).
Please could you clarify?
Thanks
Hi roydfreeman!
Sorry for this really late response, I overlooked your comment!
I mentioned in my post, solution users are deprecated in 7.0. This is not mentions in VMware document nor release notes.
I got the information from last VMworld and blog posts like this from VMware vSphere blog:
https://blogs.vmware.com/vsphere/2020/04/vsphere-7-certificate-management.html
When I got more information I will post it here.
I hope this information answers your question a little bit?
Regards
Wolfgang
Hi,
How do you fix this error you have described above?
Error occurred while fetching tls: Exception found (The provided MACHINE_SSL certificate and provided private key are not valid.)]
Thanks
Hi Tony!
You should do these steps:
1. create a CSR,
2. create a Certificate using this CSR.
When you did not create a CSR or you re-created a CSR and try to install the certificate that is based on the first CSR, you will get this error.
When you create a CSR a private key is created as well. The certificate you try to install must match this key!
I hope this helps.
Regards
Wolfgang
Thanks for the very prompt reply.
I have been confused by certificate use for sometime because there seems to be contradictory advice. For example in VMware KB 2112014 it says
“When using an external CA, the MACHINE_SSL_CERT needs to contain all certificate starting from root, like:
machine_ssl.cer: This is a complete chain of leaf + intermediateCAs(if applicable) + rootCA
Root64.cer: This is a chain of intermediateCAs(if applicable) + RootCA”
regards
Tony
Hi Tony!
This is true, the certificate you want to install must include the whole chain as well. In GUI you can put in machine- and root (incl chain) separately (Step: 4. Replace certificate). When you install certificate using CLI, just one file can be installed. In this case, certificate and chain needs to be copied into one file.
Regards
Wolfgang
This is straightforward but still not easy.
We should be able to easily import wildcard certs, tie directly to Windows CA server etc. Lot of room for improvement I think.
Agree! But compared to earlier versions, this is quite practicable.
Hello,
I followed this blog and commands and end up with this error:
Error occurred while fetching tls: the trustAnchors parameter must be non-empty
Do someone know a solution for this?
Many thanks
Best regards
Maik
At which step do you get this error?
When i entered the “machine ssl certificate” and “chain of trusted root certificate” and hit “Replace” back on the main page.
Anyone figure this out? I am stuck in the same spot.
Hello
In my Case i copied my certificates of the chain in a file and used this file for “chain of trusted root certificate”.
At my first try the chain was in wrong order so i swapt it and it worked.
Hope that helps.
Best regards
Maik
I also get:
Error occurred while fetching tls: the trustAnchors parameter must be non-empty
cannot find a sollution at all…does anyone have any clue?
Dino
Just updated my post. Error appears if your root certificate does not include all CA roots. Find the solution in the notes.
So I performed a VCSA upgrade from 6.5 to 7.0 then migrated the settings in phase 2 from my old vCenter to the new vCenter. Everything worked fine, however the new vCenter is named slightly different from the old vCenter. This caused me to get the following message “Error occurred while fetchilt tls: Invalid input certificate: The Subject of the provided certificate does not contain the correct CN value”. Any ideas on that? Maybe it doesn’t like my new vCenter’s name?
Hi Paul! The name of the vCenter OS should stay the same after a migration. What is the difference in the name?
Thanks for the article, I it weird I find no vmware kb on this.
For those with less experience with vSphere, can you change “To do so, go to Menu –> Certificate Management” to say full path there? It is Menu -> Administration -> Certificates -> Certificate Management.
Thanks for your feedback! Updated my post and added the path you suggested.
Hi,
I tried to replace as described, but I get this error, when pushing the replace button:
error occurred while fetching tls: string index out of range: -1
Did anyone get this error?
Thank you
Yes, it was solved by simply pasting the text content of the cert file into the text box instead of opening the file, not sure what specifically caused it.
you must be careful, vSphere accept only unix EOF char in files.
Good point! I use
viin ESXi for handling these files. In my experience, it normally makes the right thing!The issue is that when you download the Root CA from your Windows CA server… it’s adding an extra line after the “End Certificate” line. The UI doesn’t like that and gives you the -1 error. Remove the line or just copy and paste the text without that extra line.
Thanks for writing simple instructions that VMWare seems incapable of typing!!
😀 Thanks Monty!
Beautiful, I was getting mixed up using the web interface, wasn’t sure what was vcsa cert and what was root. The command line made it way easier. Thanks!
You are welcome! And thanks for your feedback!
I think i am lacking some understanding of how certificate and chains work.
I have followed instructions and created two certificates.
But i get this error metioned in Update section when i run the Replace procedure in vCenter
[Error occured while fetching tls: the trustAnchors parameter must be non-empty]
Can someone explain to me how the root and intermediate CA certificate works?
(Running vcenter 7.0.3 on 6.5 esxi hosts)
Hi!
Simply said, a certificate chain contains each certificate from the root to the last issuing certificate authority (CA). Normally there is a root CA and intermediate CAs. Root trusts intermediate and vice versa.
https://support.dnsimple.com/articles/what-is-ssl-certificate-chain/
A valide chain contains the certificate of each intermediate CA and the certificate of the root CA. In the context here it means you copy and past each certificate (root and intermediates) of the chain into a single file.
Hope this helps your understanding.