VMware Security Hardening Guides and how to check compliance
In times of Ransomware , security breaches and exploits it is more and more important to harden every layer of IT infrastructure. This blog post is about hardening options of VMware layers. I will describe the concept of the VMware Security Hardening Guides and how to check compliance with VMware Operations Manager.
What is VMware Security Hardening Guides about
VMware provides Security Hardening Guides for products like vSphere, NSX and Automation. Here, I will primarily talk about the vSphere Security Configuration Guide. It is available starting with vSphere 4.0 and changed over time. Latest versions are for vSphere 7.0 U3 and 8.0.
Basically the guide takes different design consideration into account:
- System Design
- Hardware Configuration
- ESXi Hosts
- vCenter
- VM Hardware
- Guest OS
Detailed discussion
For each of these categories, there are a variety of different parameters and considerations that are discussed in great detail. All aspects of a particular configuration setting are part of an Excel sheet. Where applicable, these topics are discussed:
- Implementation Priority
- Range is from P0 (important and should be changed from default) to P2 (default is secure and should be monitored).
- Description and Discussion
- What is the issue and why is it important?
- Configuration Parameter
- If it is about a certain parameter, here you can find which one it is.
- Installation Default Value
- Suggested Value
- The shown value is recommended to raise security.
- Action Needed
- Modify: change the default value to the recommended.
- Audit: monitor the value of the parameter to ensure the correctness of the setting.
- Setting Location
- Here you can find the object respectively the layer, the value needs to be set.
- Potential Impact if Default Value is Changed
- What is to expect when you change the parameter.
- PowerCLI Command Assessment
- Here you can see PowerCLI commands for querying values.
- PowerCLI Command Remediation Example
- Find PowerCLI Commands for changing values.
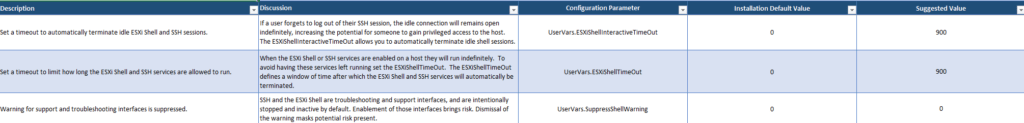
Now it should be clear how powerful this security guide is! There is not just a list of recommended values and settings, there are also arguments why you should set them and possible issues to consider when doing so. My personal highlight is, that – if applicable – the guide shows PowerCLI commands to view and change the parameters it discuss.
How to check compliance
To check compliance within your environment, you need to assess all layers of the guide and compare the current settings of each object with the guide’s recommendations. This is not something you want do by hand, believe me.
A individual way is to use PowerShell with PowerCLI module. A simpler way is to use a tool for this job. Therefore I show here how to use VMware vRealize – new name: Aria – Operations.
Check compliance with VMware Aria Operations
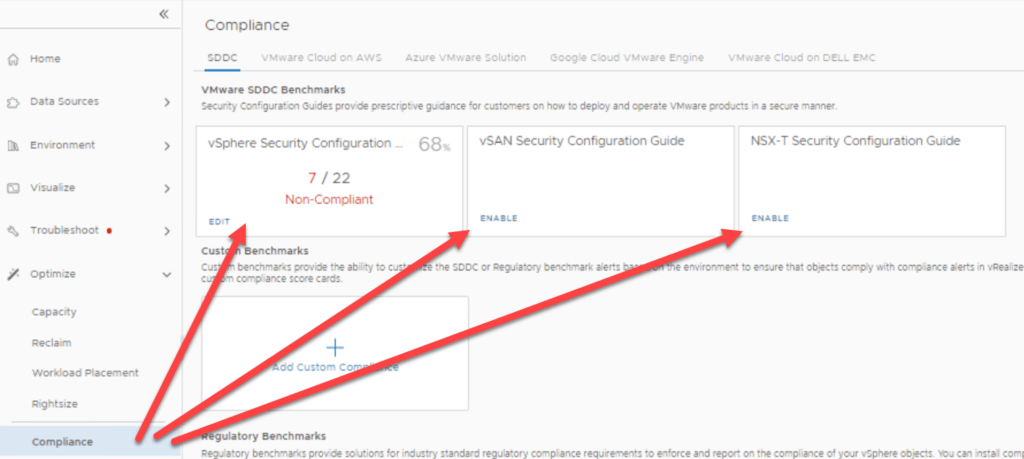
With Aria Operations it is quite simple to monitor object settings. First you need to enable Security Configuration compliance checks. To do so, open Optimize and click on Compliance. Here you can enable Configuration Guide for vSphere, vSAN and NSX.
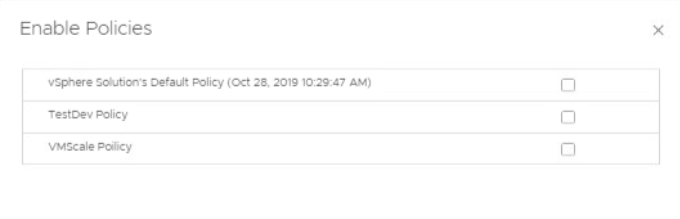
You have to select the policies you want the compliance checks attached.
System needs some time for the first assessment. Afterward you have powerful features to check compliance.
Compliance check using alerts
This kind of dashboard is situated in the Compliance section of Aria Operations. Group by Object Type to see non-compliant objects.
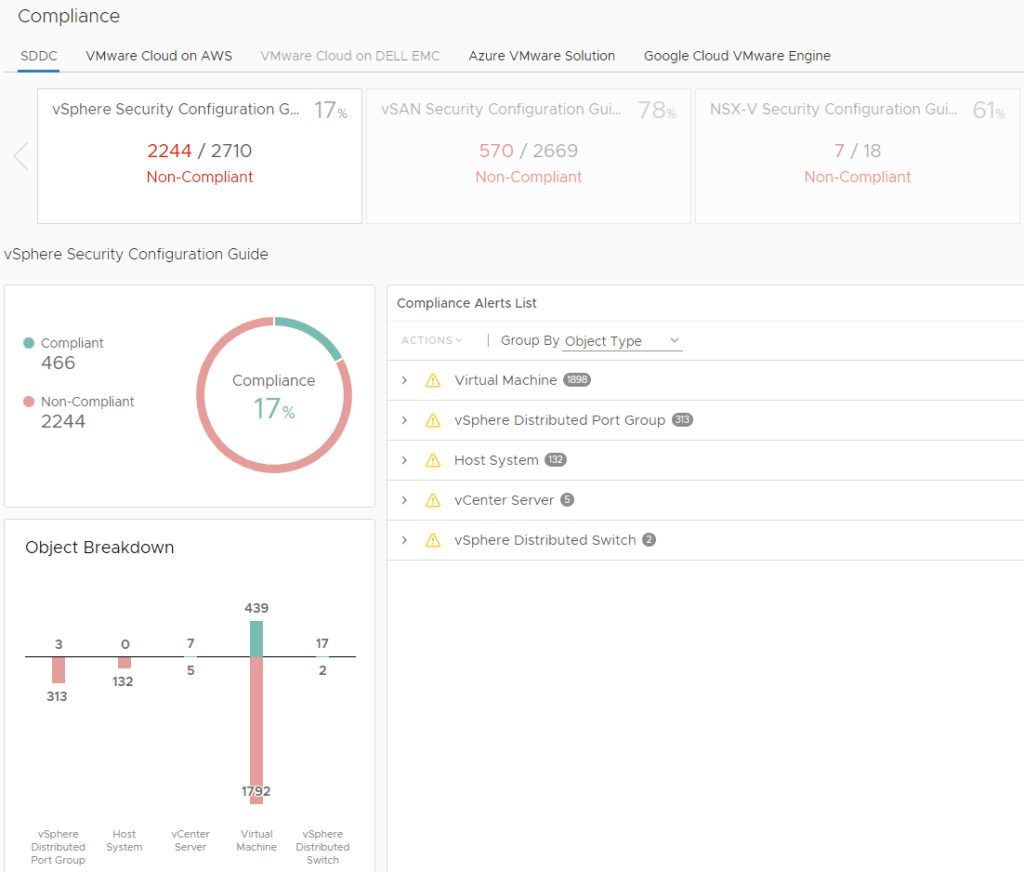
Compliance check using dashboard
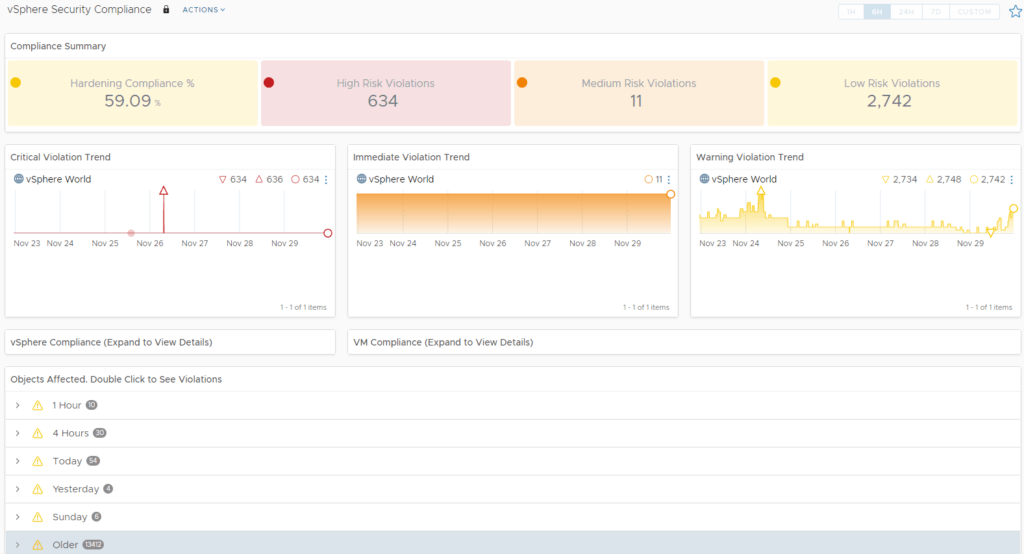
There is a vSphere Security Compliance dashboard in Aria Operations. Although it is marked as deprecated, it still works.
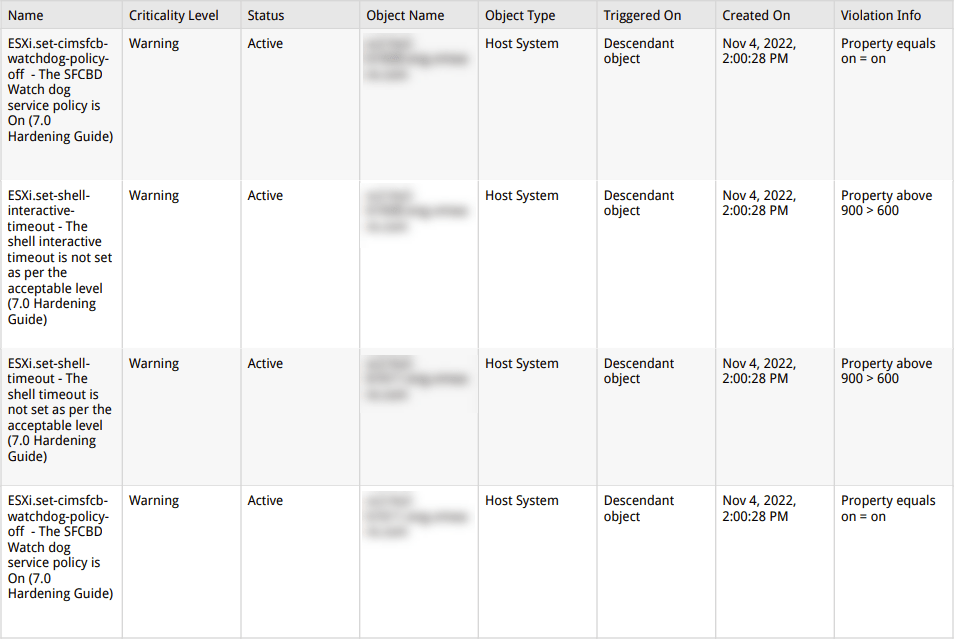
Compliance check using report
There are two report for in Aria Operations for Security Configuration Guides:
- Compliance Report – vSphere Security Configuration Guide – Non-compliance
- NSX Hardening Guide – Non-compliance Report
These reports show all objects that are not compliant. Also the settings itself that violates.
Notes
- If you do not have Aria Operations licensed, you can sign up for a free 60 day trial on-prem.
- Compliance check is also a feature in VMware vRealize Operations Cloud. It works the same way as on-prem.
- Even the current version of Aria Operations on-prem does not use the current version of the Security Configuration Guide. But this is no big deal because you can even check newer vSphere versions with older Guides. With latest October update of vRealize Operations Cloud, used Security Configuration Guide was updated too.


